Every single day, the usage of smartphones will increase, along with the development of the working system of Android. Subsequently, there have been experiences of malicious people and hackers capitalizing on the exploits that Android has to supply to realize entry to the information that customers maintain pricey. Such threats have included, for example, the Flubot malware assault that was launched for Android gadgets globally within the yr 2021. Notably, this malware focused banking apps utilized by victims on their devices to hold out the cyberattacks. That’s the reason, on the subject of the understanding of the Flubot malware’s signature and habits, our analysis focuses on the doable strategies of the cyber menace’s future strikes.
Initially, our analysis included an exploratory evaluation of three totally different samples of Flubot malware discovered within the free repository of the Hatching Triage platform.
So as to obtain this, we utilized Android Digital Gadget (AVD) as our base for testing utilizing the Android Debug Bridge (ADB) for dynamic evaluation together with BurpSuite for a similar. For static evaluation, the present samples had been analyzed with the assistance of the Cellular Safety Framework (MobSF) and Bytecode Viewer to be able to look at the malware samples’ supply code.
Believing that our conclusions may be incomplete, we explored additional into the operations of the Flubot virus and located that it delivers or locations dex information on the sufferer’s system. These information act because the framework of the malware, and the extra information are used to boost its performance. As an example, the Flubot virus disguises itself as purposes that ship messages or the Brief Message Service (SMS) on the host system. We additionally got here throughout one other variant of Flubot Malware which makes use of the Area Technology Algorithm (DGA) to create channels to speak with the C&C server.
Introduction
With the development and availability of data know-how throughout borders, this has additionally caused a corresponding improve in cybercrimes [1]. As an example, Indonesia skilled one occasion the place it had did not implement these reforms and was now managing the fallout. In response to the current findings, there have been 6 billion cybersecurity incidents reported in 2021 and it’s comprised of numerous malware assaults [2]. Malware is a time period that’s an abbreviation for malicious software program primarily for cybercrime is operational in several working methods together with, Android, iOS, Home windows, and macOS [3]. In response to the given references, the world file of cell device-based hacks until December 2021 was 2, 228, 801 [4]. Particularly, Android, with 1 million copies, is acknowledged as one of the profitable platforms. In response to Fb’s 1. 2 6 billion customers, they’ve been attacked 1,451,660 occasions by malicious Android packages [4][5]. Particularly, Flubot emerged among the many newest threats geared toward Android gadgets in 2021, originating primarily in New Zealand, Australia, France, and Germany [6][7]. One other supply of data reveals that Flubot’s main motivation is to steal data from the affected system in a course of the place it poses as an precise software [8].
Determine 1: Flubot malware unfold methodology
Methodologies for Malware Detection
Detection methodologies for malware sometimes fall into two classes: whereas there are various approaches in software program testing, two of the most typical ones are often called static and dynamic evaluation [9].
Static evaluation of malware samples means learning their code and construction with out truly permitting the code to execute, whereas dynamic evaluation refers to working the precise samples in a managed context. In essence, static evaluation invokes signature detection whereby it compares the patterns of analyzed software program with a database of different infamous purposes. Nevertheless, this method has a weak spot whereby the “bad” code could be unstructured and arduous to comply with or “obfuscated”[10]. The usage of M and P sort of malware, which has the power to alter its code in the middle of executing its operate, can’t be detected by the above strategies of static evaluation [11].
Dynamic evaluation, alternatively, investigates malware habits by runtime evaluation of the malware in query such because the API calls and system adjustments that the virus makes and registry adjustments [12]. Whereas dynamic evaluation presents a number of advantages, the basic drawback is that it necessitates creating testing environments, that are time-bound.
Hybrid Evaluation Strategy
Hybrid evaluation is one other sort of research that could be a mixture of each static and dynamic evaluation and likewise it could detect extra completely than the opposite two. Flubot is an Android malware not too long ago found out there that targets the working system of the identical title particularly. To realize static evaluation, we use instruments like MobSF — Reverse Engineering Evaluation, APKtool, Dex2jar, and JD-GUI for analyzing the malware signature and habits. As for the dynamic evaluation, we get to make use of instruments corresponding to BurpSuite, Android Digital Gadget, Android Debug Bridge, and Frida to work together with the virus to review the behavioral sample in a contained atmosphere. On this method, we want to outline the signature and behavioral patterns of Flubot malware and examine its impact on Android gadgets.
Methodology
Due to this fact, we proactively examined the Flubot malware exercise intimately, in order to realize perception into its habits and impact inside the system. For this objective, on the subject of the idea of “virtual environments,” we utilized the associated software program for information extraction that was important for figuring out our key findings. On this qualitative potential examine, APK software information affected by Flubot malicious malware are examined with three randomly chosen samples examined for evaluation.
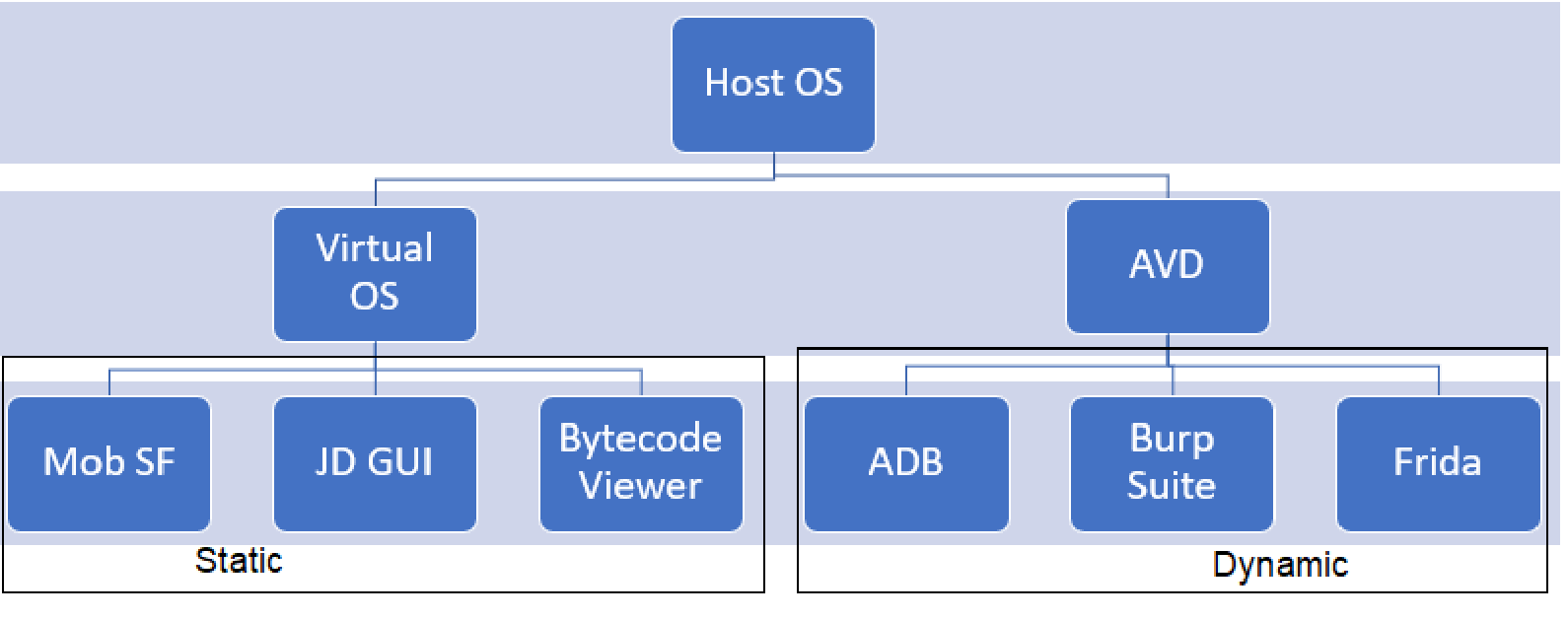
Determine 2: Malware evaluation instruments
Flubot is malicious software program or malware designed to operate secretly and has little or no file that signifies its presence. Nevertheless, there are particular indicators that the presence is indicated corresponding to fixed use of voicemail software that appears pretend, any supply service like FedEx or DHL, automated steady sending of quick messages to contacts, and different distortion of the settings of the cell system.
1. Establishing a Testing Setting
They are going to be mentioned within the subsequent part, the place we have now delineated the instruments which can be wanted and have created a web-based context for analysis. This was achieved to make sure that the contamination by malicious packages within the community was restricted to a separate atmosphere inside the community system.
2. Hybrid Evaluation Strategy
I known as the method to figuring out the options a hybrid evaluation method as a result of we used each static and dynamic analyses to perform the duty. Determine 2 reveals the algorithm of the employed methodology.
3. Instruments Utilized Evaluation
- Host atmosphere: This report seeks to current the findings of the evaluation of statistical information and key traits of the Home windows 10 working system, the place the important thing factors embrace:
- Digital environments: Android Digital Gadget (AVD) is an Android emulator the place customers get an opportunity to reside on the earth of Android and expertise its options and features whereas Kali Linux is a Debian-based Linux distribution, designed for superior penetration testing and safety evaluation.
- Static evaluation instruments: MobSF – Though JD-Gui can not disassemble code attributes, Bytecode Viewer is a wonderful software for analyzing courses and code attributes, and utilizing the 2 devices collectively could be environment friendly.
- Dynamic evaluation instruments: ADB and Frida, BurpSuite
4. Execution of Evaluation
- Configuration of AVD: Android stood out as a picture acceptable for working the Flubot malware, and for creating the AVD virtualization engine. For this picture, we selected one from Google Nexus, utilizing the Android working system model 8. 0 API 26.
- Static Evaluation
- MobSF: They’re sometimes used for extracting the manifest XML file paperwork from APK samples to be able to analyze the latter for information on the intentions and permissions of the malware in query.
- Bytecode Viewer: Bytecode Viewer is downloaded on the Kali Linux to reverse engineer and analyze the supply code from the dex information.
- Dynamic evaluation:
- Execution of malicious purposes: By infecting the AVD with malware samples and analyzing their habits in real-time, additional experimentation was carried out based mostly on the set up of precise samples of the malware on the AVD and following the execution they carried out in real-time mode.
- Monitoring instruments: ADB and Frida had been utilized in monitoring Flubot malware exercise; BurpSuite was used to find out whether or not the engine recognized system calls and analyzed all web site visitors generated by the malware. Determine 3 offers an summary of the group of our framework for malware evaluation.
To this finish, we discovered it essential to undertake a extra holistic method to understanding Flubot malware’s signature, habits, and results on the system being explored; the Android working system, on this case.
Determine 3: Strategies of malware evaluation
Configuration and Setup
For interception and evaluation functions, we arrange a proxy listener at BurpSuite and included the best AVD proxy. On the AVD, proxy settings had been configured manually, utilizing the identical proxy hostname and port quantity as these arrange within the BurpSuite listener. Then a CA certificates accessible on the BurpSuite web site must be put in on each the BurpSuite host pc and the AVD emulator for a safe connection to be created. Initially after finishing the setup of BurpSuite, it was able to seize the AVD site visitors.
Outcomes and Dialogue
A mixed examine of static and dynamic evaluation was carried out on Flubot samples obtained from the Hatching Triage platform utilizing open-source intelligence methodology. Scanning carried out by the MobSF software introduced out the next: with a safety rating of 48/100, its danger score was estimated at a medium stage. Having examined the Indicators of Compromise (IoC) for the samples of the malware, extra traces had been recognized on the Android-based methods such because the bundle title or the APK hash.
The second sort of permissions posited for additional examination originated from the Android Manifest within the XML kind and recognized 15 permissions out of that are permissions to entry the web, SMS, contacts, and telephone calls. A number of the key permissions included QUERY_ALL_PACKAGES, which facilitates stock of put in purposes on the system, and REQUEST_DELETE_PACKAGES, which permits the uninstallation of purposes put in on the system.
Desk 1: Indicator of compromise from the angle of the three areas of data administration specifically: assortment, processing, and distribution.
The string evaluation revealed purposeful data inherent within the construction of the malware. These embrace communication with C&C servers, technology of random domains, and connection testing on gadgets. The static mechanism in reference to the dynamic evaluation in a digital situation confirmed the efforts made by the malware in making an attempt to put in its payloads and additional clone the real software such because the messaging software.
Desk 2: Permission record in pattern
An evaluation of the site visitors recognized rare connections to C&C domains created by utilizing the Area Technology Algorithm (DGA). Information obtained from contaminated gadgets was reported to incorporate textual content messaging data and information associated to cryptocurrency utilization.
Conclusion
The remark of Flubot malware samples uncovered permissions to seize delicate information, command communication with domains, and doable payloads that will have an effect on purposes for cryptocurrency. Resulting from its skill to sneak in and stay undetected in a pc system, it is suggested that the malware be prevented by cautious use of the Web. Being cautious to not click on on suspicious hyperlinks or set up any purposes originating from presumably compromised web sites or random emails, Flubot malware could be prevented because it largely spreads by spam or phishing reasonably than getting by app markets corresponding to Google Play.
References
- M. Ribka Akhyari and A. Rizal Pratama, “Peranän Perlunya Kepedalian akan Ancaman Serangan Berbasis Backdoor pada Pengguna Smartphone Android,” Automata, 2017. 2, no. 1, pg. 7, 2021, [Online].
- Badan Siber dan Sandi Negara, “Laporan Tahunan Monitoring Keamanan Siber 2015,” pg. 54–55, 2022, [Online].
- A. Take a look at, “Malware Statistics & Trends Report,” Magdeburg, 2021. [Online].
- D. Maslennikov, “IT Threat Evolution: The next quarter, Q1 2021,” July 2015 [Online].
- S. R. Division, Statistic, Android by Statistics and Details, Statista Infographics Obtainable from statista.com. 2018, [Online].
- Flubot scams, Scamwatch, accessed third January 2021. Textual content message rip-off infecting Android telephones with FluBot _ CERT NZ, New Zealand, on October 1, 2021, accessed on October 2021.
- V. D. M. T. Mark, “FluBot Malware – All You Need to Know & to Act Now,” 2021.
- S. Arshad, M. Ali, A. Khan, dan M. Ahmed, “Android Malware Detection & Protection: A Survey,” Int.
- BPPT, “Guideline of Handling Malware Incident,” Insid. malware, pg. 1–39, 2018.
- Y. Zhou dan X. Jiang, “Dissecting Android malware: “Characterization and evolution,” Priv. , no. 4, pg. 95–109,2012, doi: 10. 1109/SP. 2012. 16.
- A. F. Febrianto; A. Budiono; Studi; Informasi; F. R. ; Industri; S. P. Telkom; P. Menggunakan; Analisis; Malware; Community; Visitors; Android; Operasi; “Metode,” vol. 6, no. 2, pg. 7837–7844, 2019.
- G. Aaron dan C. Strutt, “Malware Landscape 2021 A Study of the Scope and Distribution of Malware,” no. November 2021.
- N. C. S. Heart, “FluBot – Android Text Message Scam,” United Kingdom: January 2021. [Online].
- M. F. Zolkipli dan A. Jantan, “Malware Behavior Analysis: Schettini, Andrea, and Riccardo. Learning and Understanding Current Malware Threats,” Proceedings of the 2nd Worldwide Convention on Community Functions, Protocols and Providers, NETAPPS 2010, 2010, hal. 218–221, doi: 10. 1109/NETAPPS. 2010. 46.
- Ok. Demertzis & L. Iliadis, “Evolving smart URL filter in a zone-based policy firewall for detecting algorithmically generated malicious domains,” Lect. Notes Comput. Sci. (historically collectively known as I, e. g., LNCS, Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. Afonin DN № 9047 October 2016 p. 223–233, 2015, doi: 10. 1007/978-3-319- 17091-6_17.
- D. Uppal, V. Mehra, and V. Verma, “Basic survey on Malware Analysis, Tools and Techniques,” Int. J. Comput. Sci. Appl. , vol. 4, no. 1, pg. 103–112, 2014, doi: 10. 5121/ijcsa. 2014. 4110.
- M. Sikorski dan A. Honig, Sensible malware evaluation: the reside, sensible method to pulling aside viruses, worms, Trojan horses, and different types of malware. No. Starch Press, 2012.
- M. Zaman, T. Siddiqui, M. R. Amin, and M. S. Hossain, “Malware Detection in Android by Network Traffic Analysis,” in Proceedings of 2015 Worldwide Convention on Networking Techniques and Safety, NSysS 2015, 2015, doi: 10.
- M. Ali Egele, Thijs Scholte, Evren Kirda, and Christopher Kruegel, “A Survey on Automated Dynamic Malware-Analysis Techniques and Tools,” ACM Comput. Surv. , vol. 44, no. 2, 2012, doi: 10.
- A. Kosasih, Febriansyah, T. Sari, I. Harahap, A. N. Jamaludin, A. F. Febrianto, and A. Budiono, “Pemerintaan yang Efektif, Techno, Perencanaan dan Pengendalian Keuangan daerah, Future,” 2018, vol. 6, no. 2, pg. 7837–7844, 2019
- Samir M. pair/Touseef Juithi, A. Bilal, “FluBot – Malware Analysis Report,” Phishing Malware, Switzerland, 2022. [Online].