Securing info is essential as cyber-attacks are getting extra refined. Knowledge residing in an unprotected state at relaxation (databases, saved recordsdata, and backups) pose probably the most important dangers.
Knowledge at relaxation encryption is important to ensure that info is secure and unreadable even within the occasion of unlawful entry. This dialogue highlights why encrypting knowledge is seen as an indispensable a part of bolstering total cyber safety and protecting property secure from undesirable entry.
Deciphering Dormant Knowledge
Not like knowledge in transit, the place knowledge is repeatedly transferring between techniques and over networks, knowledge at relaxation refers to info that exists on a chunk of {hardware} or inside any digital storage system.
Their backup techniques have a completely completely different set of safety challenges to maintain out malicious actors versus knowledge in transit that’s protected by way of well-defined protocols throughout motion.
Picture Supply
Examples of information at relaxation embrace recordsdata on laborious drives, structured organized teams of information (together with database tables), and archived backups. This knowledge could possibly be out there by way of alternate apps or interfaces which are static.
Varonis’s World in Knowledge Breaches report acknowledged that 7 million unencrypted knowledge information are compromised every day. Knowledge at relaxation is obligatory in some sectors reminiscent of healthcare and finance. This ensures that it meets relevant rules like HIPAA, offering safety to healthcare trade knowledge. It additionally secures non-public monetary info in finance towards theft and illegal use.
Authorities entities make use of sturdy encryption to safeguard confidential info and stop unlawful entry. Knowledge at relaxation safety stays a linchpin to a full spectrum of cyber safety.
The Rising Risk Panorama
A urgent subject in cybersecurity developments is the rising array of high-level assaults being aimed straight at knowledge at relaxation. A few of these applied sciences are at present being utilized by hackers.
Malicious actors can encrypt the victims’ knowledge and maintain it for ransom thus denying them entry, or promote confidential info. Moreover, social engineering assaults are sometimes employed to trick people into revealing delicate info or credentials. Within the case of ineffective data-at-rest encryption, these assaults can lead to a large-scale breach that places non-public info organizations in danger.
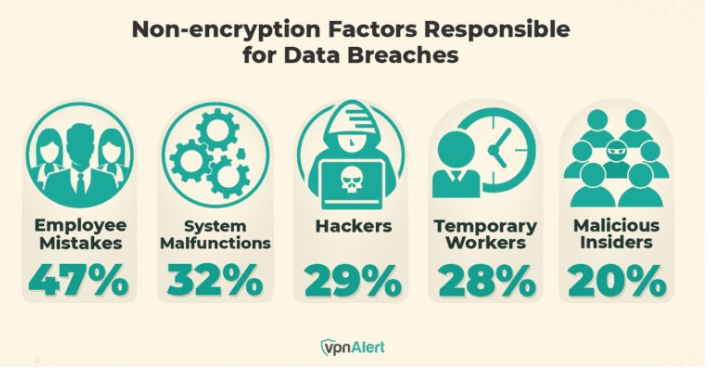
Picture Supply
The hazards linked to unprotected knowledge at relaxation are sharply delivered to gentle by the Capital One knowledge breach of 2019. On this incident, greater than 100 million private particulars of the financial institution’s shoppers had been leaked when a hacker breached the establishment’s cloud-stored knowledge as a result of a misconfigured firewall. The assault’s impression may have been considerably lowered by stronger knowledge storage encryption that may make the stolen info nugatory with out the decryption key.
The repercussions of information at relaxation compromise are catastrophic; companies could expertise monetary losses straight by way of fines and authorized charges and not directly by way of destructive model recognition and lack of shopper belief.
Moreover, as the method of recovering after such hacking sometimes entails pricey implementations of latest safety techniques and processes, the implications for an organization’s every day functioning in the long run are extreme. Any enterprise that seeks to defend its most significant property from an escalating hazard profile should begin implementing data-at-rest encryption at the moment. That is now not an choice.
How Knowledge at Relaxation Encryption Works
Shielding inactive knowledge saved on bodily units reminiscent of laborious drives, databases, or cloud storage requires data-at-rest encryption. It ensures that nobody can learn or take advantage of this saved knowledge when uncovered to illicit attain with out appropriate encryption keys. That is the way it works:
A. Encryption Algorithms
Two essential algorithms are employed in encrypting saved knowledge. They’re:
Symmetric Encryption
This system makes use of a single key for each encryption and decryption. It’s a quick strategy and useful for big datasets. However the issue lies in sharing the important thing between events safely.
Picture Supply
Uneven Encryption
This encryption method makes use of two keys, the general public key to encrypt and the non-public key to decrypt. This technique improves safety by eliminating secret keys that must be shared although it’s slower.
Picture Supply
B. Encryption Keys
Saved knowledge encryption safety is extra depending on the security of the entry keys. Sturdy key administration processes reminiscent of safe storage, rotation, and entry management are required to be in place. Key safety ensures the info stays ineffective even when encrypted knowledge is stolen.
The most effective password managers are among the many best key safety additions you may make. It’s useful to have these instruments and assist you to retailer the keys securely guaranteeing that none apart from approved personnel can entry them.
C. Implementing Encryption
Knowledge at relaxation is encrypted utilizing two essential strategies: Software program-Based mostly Encryption and {Hardware}-Based mostly Encryption.
Software program-based encryption means specialised software program used to avoid wasting knowledge to any system. One of these knowledge encryption is customizable and could also be used for varied storage techniques. Nevertheless, software-based encryption techniques require processor energy to encrypt knowledge themselves, which could increase latency and system points.
The second kind is hardware-based encryption, constructed into {hardware} storage itself. This system encrypts and decrypts info extra rapidly and calls for fewer system sources. Self-encrypting drives is an instance.
Regulatory Compliance and Knowledge Safety Legal guidelines
No doubt, compliance and knowledge safety are essential. Requirements reminiscent of GDPR(Normal Knowledge Safety Regulation) and HIPAA (Well being Insurance coverage Portability and Accountability Act), have made the safety of delicate info an integral half. These legal guidelines dictate powerful knowledge safety measures for private and well being info.
Knowledge at relaxation encryption is crucial to make sure compliance with these mandates. When knowledge is encrypted at relaxation, companies can safe their saved knowledge in case of a breach the place unauthorized entry has been correctly managed. This helps preserve delicate knowledge inaccessible to anybody with out the suitable decryption keys, and due to this fact compliant with GDPR privateness guidelines and HIPAA protections for private well being info.
Encryption is employed by 42% of respondents for buyer knowledge, rating it because the fifth mostly encrypted kind of knowledge in companies. Implementing knowledge at storage encryption helps in regulation and most significantly the belief of consumers.
Companies can strengthen buyer relationships by investing in defending private info. On the similar time, sturdy safety techniques stop fines and authorized points on account of knowledge leaks, in the end saving organizations from monetary losses and reputational harm.
Integrating Knowledge at Relaxation Encryption right into a Complete Safety Technique
Static knowledge encryption suits seamlessly right into a defense-in-depth technique by offering a further layer of safety. Whereas firewalls and intrusion detection techniques (IDS) safeguard towards unapproved community entry and monitor suspicious exercise, encryption ensures that even when these shields are breached, the info stays inaccessible. Encrypting knowledge at relaxation provides an important safeguard, rendering stolen or intercepted knowledge unreadable with out the correct decryption keys.
Encryption enhances firewalls, IDS, and multi-factor authentication (MFA). Firewalls defend towards unsanctioned entry from the surface, and IDS detects and alerts customers to potential threats, whereas MFA gives extra id authentication for person account entry. Blockchain expertise additional enhances this safety framework by providing a decentralized ledger that ensures knowledge integrity and transparency, making it practically unattainable for unauthorized events to change info.
Combining them is a holistic safety resolution. Due to this fact, encryption retains any info intercepted secure; firewalls and IDSs however assist safe the info from being accessed or exploited within the first place.
Saved knowledge encryption mixed with different safety components strengthens total knowledge safety thereby minimizing danger. It constructs an entire resolution for exterior assaults and inner knowledge safety offering full-fledged safety towards normal threats or potential inside jobs. Embedding encryption into a bigger safety technique creates an adaptable safeguard that narrows the assault floor and strengthens knowledge towards many sorts of threats.
Securing the Basis of Knowledge Safety With Encryption
On this period of rising cyber threats and knowledge breaches, encrypting knowledge at relaxation is a vital further layer of protection. Encrypting at relaxation secures saved knowledge by defending towards unauthorized entry offering improved security, compliance, and privateness of the info.
On account of growing cyber threats, it’s turning into more and more crucial fairly than non-compulsory for organizations to ascertain themselves with encryption options to safe their property and keep confidence inside the digital realm.