AI/ML instruments and applied sciences closely affect the fashionable digital panorama by introducing quite a few use circumstances involving AI-based malware detection, stopping social engineering assaults, and risk identification and remediation. Many organizations have acknowledged AI/ML’s prominence within the cybersecurity risk panorama and have began to leverage AI/ML of their enterprise and safety necessities. AI/ML-based options help staff to finish their day-to-day duties extra effectively and very quickly. Nevertheless, on the similar time, we’ve got additionally witnessed an exponential enhance within the cybersecurity risk panorama. Therefore, cybersecurity professionals and software program builders have additionally began utilizing AI/ML to construct extra revolutionary, adaptive, and strong techniques and purposes to guard a corporation’s IT and community infrastructure.
Statistics: AI/ML in Cybersecurity
In current instances, we’ve got witnessed the widespread adoption and exponential progress of AI and ML applied sciences. Beneath are the statistics taken after thorough analysis highlighting the influence of AI/ML instruments and strategies on cybersecurity risk detection and growing general cybersecurity efficiency.
- Statistics present that the worldwide AI software program market at the moment generates round $100 billion in income, which is anticipated to develop within the coming years.
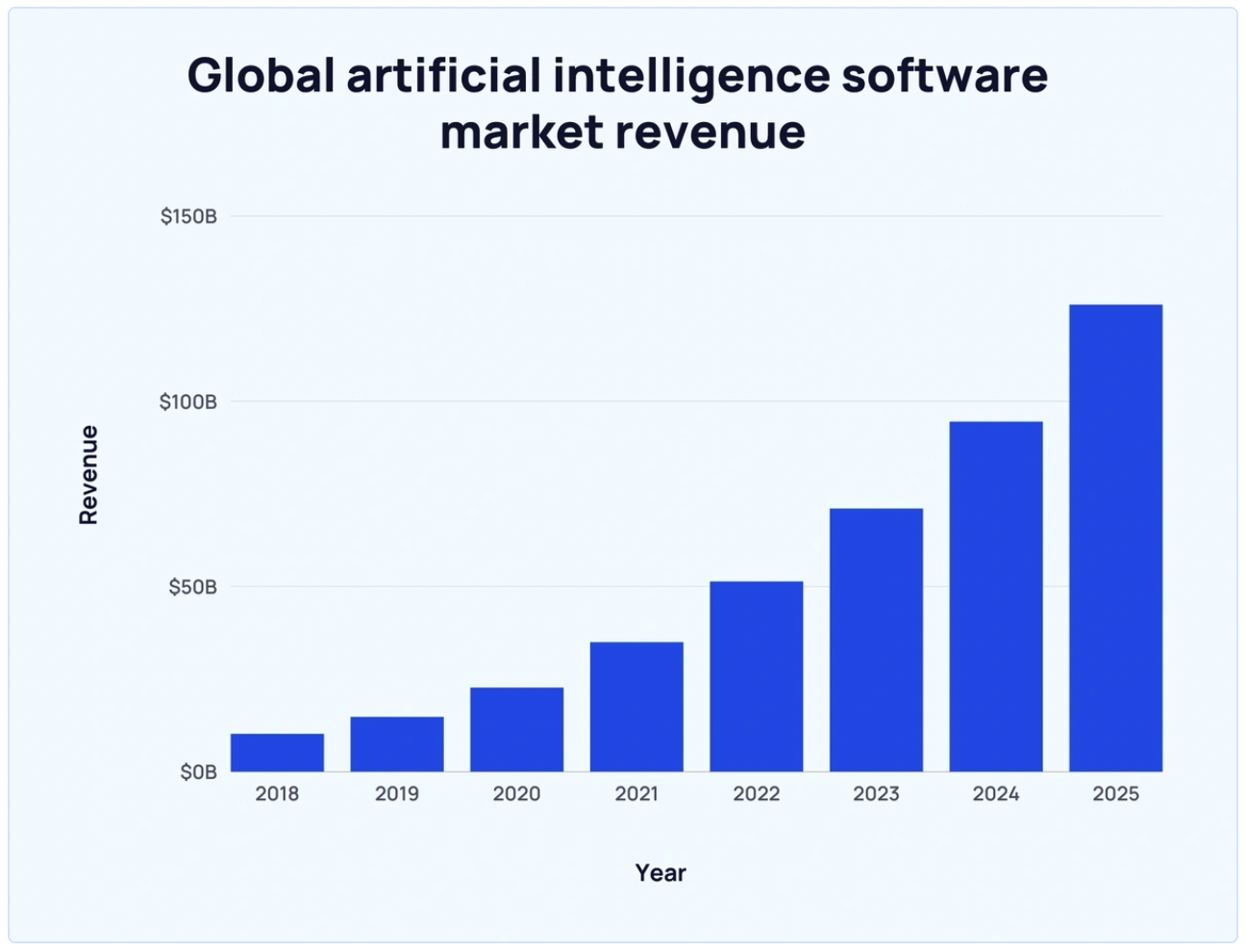
(Supply: Exploding Subjects)
- In accordance with the International State of Safety Operations report, AI/ML powers 93% of SOCs (Safety Operations Centres) for risk detection.
- In accordance with a report by Capgemini, 69% of organizations imagine they will not be capable of reply to essential threats with out AI. Moreover, 73% of organizations already use AI to help in safety operations.
- In accordance with a report introduced by Statista, the marketplace for AI in cybersecurity is anticipated to point out appreciable progress within the coming years, from round 24 billion U.S. {dollars} in 2023 to roughly 134 billion U.S. {dollars} by 2030.
- In accordance with a Cisco 2024 Information Privateness Benchmark Examine, 79% of organizations are getting very important or important worth from GenAI.
AI/ML in Cybersecurity Risk Detection: Use Circumstances
Nobody can deny the numerous influence that AI and ML options are going to have on cybersecurity risk detection. AI/ML helps swiftly detect and reply to cybersecurity threats in a dynamic and sophisticated cyber panorama. These superior methodologies provide key advantages like automated workflow, decreased human intervention, accuracy, minimizing false positives, and rather more. Let’s discover some key use circumstances of AI-driven safety options in enhancing cybersecurity risk detection.
1. AI-Pushed Safety Operations Facilities (SOCs)
A SOC’s day-to-day duties embody risk monitoring, researching diversified log datasets, detecting and figuring out threats, and offering remediation steps to decrease the influence of safety incidents. AI/ML options can assist automate and streamline these substantial processes, general growing the effectiveness, resiliency, and accuracy of SOC techniques. Builders and safety professionals can work on creating and coaching AI/ML options that may detect superior threats, together with zero-day assaults and sophisticated malware, and analyze the malware in opposition to unknown assault signatures and/or anomalies that conventional techniques are certain to overlook.
2. Identification of Social Engineering and Phishing Assaults
AI is revolutionizing the detection and prevention of social engineering and phishing assaults. Anti-phishing instruments are actually evolving by leveraging AI/ML to acknowledge patterns and behaviors. These fashions play a vital function in predicting and stopping phishing assaults whereas analyzing giant datasets (each structured and unstructured) to investigate patterns and create assault signatures, consequently easing the early identification and remediation of such assaults.
3. Assault Signature and Anomalies Identification
Assault signature identification requires a singular set of methodologies and strategies for which AI/ML fashions are tailor-made. These fashions are wonderful at figuring out assault signatures by analyzing huge quantities of historic and real-time information curated from diversified sources, together with structured and unstructured information. They assist acknowledge identified assault patterns whereas additionally adapting to establish beforehand unknown signatures, serving to safety techniques keep forward of rising threats. AI can be utilized to detect anomalous actions like unauthorized information entry or privilege escalation, serving to stop information breaches from inside actors.
4. AI leveraged Predictive Analytics and Risk Intelligence
AI/ML options, when leveraged with predictive analytics and risk intelligence strategies, can allow organizations to forecast potential threats and/or cybersecurity incidents. These techniques are well-trained in opposition to datasets revolving round techniques utilized in previous assaults to foretell future vulnerabilities, permitting for proactive risk identification and mitigation and strengthening general safety posture.
- AI/ML options also can considerably scale back the variety of false positives and permit safety researchers to deal with the reputable risk. These fashions practice themselves on historic information, growing their accuracy with every part.
- AI-powered options assist organizations keep forward of dynamic threats by incorporating AI-driven predictive analytics and risk intelligence, which may anticipate potential assaults by analyzing huge quantities of information already obtainable
5. Earlier Malware Detection
Earlier, anti-virus or malware detection techniques closely relied on identified patterns or behaviors depicted by malware, explicitly often called “attack signatures.” Nevertheless, this system makes these options much less efficient in opposition to zero-day malware assaults. AI fashions can analyze hundreds of thousands of samples of malicious and benign information and may detect even the delicate indicators of virus actions or new malware variants that haven’t but been cataloged. AI/ML instruments can considerably improve the tempo of response outcomes when encountering cybersecurity incidents, as they automate real-time risk detection and mitigation methods.
6. Insider Risk Detection
AI/ML-based options can simply be leveraged to detect and establish the potential presence of insider threats. These fashions can assist monitor person habits and establish anomalies that appear suspicious in nature when in comparison with established patterns. Makes an attempt to suspicious actions like unauthorized entry, information exfiltration, insider-driven breaches, and so forth., will be detected in real-time, considerably minimizing the influence of cybersecurity incidents. These options can scale as much as higher depths effortlessly and seamlessly, dealing with large volumes of information to investigate and reply to any inside threats.
Remaining Phrases
On the approaching finish, one can not deny the optimum and refined outcomes produced by AI and ML instruments and applied sciences when uncovered to cybersecurity risk detection duties and general enhancement of safety posture. These applied sciences provide unparalleled benefits resembling resilient cyber risk detection capabilities, quicker response instances, decreased false positives, and curation of dependable and optimum assault signatures to establish current (identified) cybersecurity threats. We are able to keep one step forward of rising dangers and risk vectors by leveraging ideas of AI/ML in our end-to-end enterprise operations. This dependence on AI/ML options is certain to extend within the upcoming years as these cyber threats proceed to develop and evolve, ultimately turning into a vital enterprise part for contemporary cybersecurity methods.